After reading my previous blogs ( blog1 and blog2 ) , you might be wondering if open source/free software/community development model helps to create a better software? and I am going to shed some light on it in this post.
Before going to further discussion, I want to to talk about community development model. In a Community development model anybody can participate in the software development irrespective of race, religion, nationality, gender, educational qualification and social status. Anybody who uses the software, develops the software, does bug fix, creates documentation , maintain the infrastructure for the project and contributes to the success of the project is part of the community. In a community project , community decides the road map for the project. This actually changes the nature of the project. We will discuss about how the nature of the project changes in further discussion. However, for the community i.e. everybody to participate in the project, the source code must be made available to them and this is how source code availability becomes a very important and a bare necessity . Source code access i.e. open source is a precondition for community development model. Without access to the source code, we can’t follow a community development model.
I am not sure if all of you understand how a software is developed in a company .If you understand it, you can skip the below paragraph. Else lets first discuss how typically a software product gets developed in a proprietary company. Then we will compare how it is different from community development.
A company sells software to solve a problem or a set of problems or a better solution over an existing one. Before selling the product , they develop/create it. As part of the development process , they hire people to do market study/research on what are the competitive products available for solving the problem, what they are also trying to solve ? What should be their approach to the problem? Then they hire software engineers, put them to a RnD lab or “a development lab” to create it. These engineers are responsible for writing code and testing for the product. They are not allowed to share the information about the product , the code with outside world. When they are done with development of the product and it is ready, the company starts selling it to its customers. After the 1st version of software, there might be new requirements for new features, improvements to be put in to the product for the consequent versions of the software to make it better or make it competitive with other similar products. So that the company can make more profit selling it.
However an opensource/community project usually get started by an individual or a group of people initiative to solve a problem for themselves. However they make the source code available for others, in the belief that it will be helpful for others too. If others find it useful, they use it. When people use a software, they might find issues with it. They report the issues to the developer group or they fix it themselves. Some of them add new features to it according to their need. As a gratitude of the initial help they received as form of the software , they merge the new code/feature with the original software and make it available for others to use. Gradually a community is formed. Person having interest and most knowledge in the project take up the role of maintaining the project. A maintainer essentially is a project leader whose responsibility is to oversee the project growth, to collaborate among community members, to understand expectation of the community on the project among lots of other things. As the project grows, community members decide which features need to be put in to the software, which hardware they want to run it, what would be the future road map in a democratic way. This leads to development of features which people need most i.e. which solves their problems, not some fancy feature which some company executive thought would be useful for them. This also leads to better support for a wide ranging hardware as it is easier to port the code for the community members to different hardware when the source code is available. Where as proprietary companies support selective hardware which give them maximum user base and profit. But in community we need to support everybody’s hardware so that everybody should be beneficial from it, rather money or profits.
Most of the time open source/community software has better inter portability with other open source software because the goal is to collaborate, get benefited from each other which ultimately benefits the community. This leads to better integration between different software projects with each-other and result in a better product or software ecosystem. However this is not the case with proprietary software. Their decision depends on profit margin, future scope, relationship with each other (i.e. if the software are from different companies) and so on. Have you stared seeing the difference? 🙂
Even though community projects start with minimum required features but it gradually becomes a incubation ground for innovation or new ideas. Researchers, academicians, computer scientists, corporations, governments use existing open source projects to develop something new for their purpose. Lets take an example. A computer scientist doing research on distributed computing and he came up with a new algorithm which improves distributed computing. Now he want to implement and test his algorithm. Does he need to develop a new distributed system to implement his idea? or put his algorithm to a existing open source distributed system.The answer is pretty simple. He takes source code from a opensource project (something like Linux/GNU here), implements his algorithm into it. However it depends on him whether he wants to merge the code into the existing code base and make it available for others or he want to keep it to himself. But almost in most of the cases people give it back to the source, from where they took the initial code. Giving code for free doesn’t mean they are not gaining anything. A code in a popular community project gives far more credibility, popularity, reach, respect to the author along with his research publication and still if he wants, he can create money out of it . There are lots of examples of Phd papers/subjects becoming famous community/opensource/free software projects.
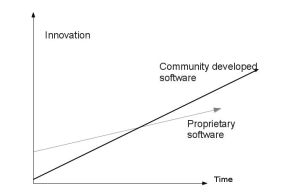
The graph shows how community developed software overtakes proprietary software in-terms of innovation in long run.
I copied the below lines form Debian Linux/GNU’s about page [1]
You may be wondering: why would people spend hours of their own time to write software, carefully package it, and then give it all away? The answers are as varied as the people who contribute. Some people like to help others. Many write programs to learn more about computers. More and more people are looking for ways to avoid the inflated price of software. A growing crowd contribute as a thank you for all the great free software they’ve received from others. Many in academia create free software to help get the results of their research into wider use. Businesses help maintain free software so they can have a say in how it develops — there’s no quicker way to get a new feature than to implement it yourself! Of course, a lot of us just find it great fun
When you are in a culture where others help you without any selfish motive, your attitude towards others also changes. You become helpful to others too. However not everybody is kind enough to give back the enhancement they make in the source code. For those we have open source licenses like GPL[2] to force them to give it back to the the community which gave them the initial source code if they are selling/commercializing it with enhancements.
Some times organisations contribute to community projects or starts community projects e.g: Linux/GNU, Mozilla firefox, Fedora, Open suse, Chrome, openstack, Xen virtualization, because they understand the benefit of community development model . We have examples of individuals or group of people/companies starting in open source projects.
Following are the positive sides of a community driven/free software/opensource project.
- More choice of hardware, platform. Most of the open-source software projects support all possible hardware.
- The life span of the software will be very long. As it is easier to fix and contribute a feature rather then creating a new project/software.
- It will be easier to customize open source software according to your needs and taste. You can remove unwanted features. That will make its IT foot print optimal.
- It wont have virus, spyware as the source code is available for everyone to see and any suspicious code never gets into the project or can be easily removable.
- Better inter portability as it is easier to integrate it with other software.
- The quality of the code in open source projects are far better then closed source ones as code is reviewed/read by more people. Also the source is better modular because of its distributed way of development.
- Helps to spread knowledge as source code is a great source of knowledge. You can learn from others work.
- It helps to avoid vendor lock in. If any company giving you commercial support for a open source/free software, they can’t show monopoly on the software. You are always free to move the support to some other company or hire engineers to support the software as the source code is publicly available.
- Cost is always less for community driven software when you need commercial supports for the software. This helps organisations to cut down their IT cost which in turn lowers the cost of their product or service.
- Minimizes software piracy. The model allows everybody to use the community version of the software with no cost, so no need of piracy.
- Does not take away freedom of users regarding how they want to use it or where they want to use it.
- Helps to create better culture, where collaboration with others plays a key role.
- Encourages innovation as there is no need to reinvent the wheel again and we can focus on new stuffs.
I am quoting Linus Torvalds on open source. He has actually summarized it nicely.
“Me, I just don’t care about proprietary software. It’s not “evil” or “immoral,” it just doesn’t matter. I think that Open Source can do better, and I’m willing to put my money where my mouth is by working on Open Source, but it’s not a crusade – it’s just a superior way of working together and generating code.
- It’s superior because it’s a lot more fun and because it makes cooperation much easier (no silly NDA’s or artificial barriers to innovation like in a proprietary setting), and I think Open Source is the right thing to do the same way I believe science is better than alchemy. Like science, Open Source allows people to build on a solid base of previous knowledge, without some silly hiding.
But I don’t think you need to think that alchemy is “evil.” It’s just pointless because you can obviously never do as well in a closed environment as you can with open scientific methods”

The topic is a very big one and it is hard to discuss it in a single blog post. It is very much possible that I may have missed some obvious points. So if you have any suggestion , kindly put them in comments. I would be happy to pick them and put it into the post.
[1] http://www.debian.org/intro/about#what
[2] http://www.gnu.org/licenses/gpl.html


